The internet was initially envisioned as a medium for the free flow of information and knowledge—hence its early description as the “information superhighway.” But governments and corporations have realized that such an outcome is deleterious to their interests.
That’s why the open and unrestricted internet is only available in a handful of countries now. Most others engage in censorship.
What is internet censorship?
In a nutshell, internet censorship refers to the control of content on the web. This implies that certain bodies have the power to determine what websites residents of the country can visit or the kinds of topics they’re allowed to publish. Internet censorship is usually motivated by moral or religious objections, or if it’s deemed anti-state.
To understand internet censorship, we must first go back to the development of the initial protocols of the web: the Transmission Control Protocol / Internet Protocol (TCP/IP).
The goal of TCP/IP was to connect multiple networks and to facilitate the development of an open architecture unencumbered by geography. Work on TCP/IP began so that each network could operate independently without impacting the stability of the web.
[Learn more about digital freedom. Sign up for the ExpressVPN blog newsletter.]
TCP/IP was brought to life with the notion that the internet should have no centralized body keeping an eye over its communication or contents. Open architecture networking was fundamental. Unfortunately, while TCP/IP has been vital to the growth of the internet itself, it has also paved the way for a number of the censorship techniques we see in use today.
The history of the internet is fascinating in and of itself, but we won’t get into too much detail about it. What’s important to note is that Tim Berners-Lee, the man widely credited with founding the internet, envisioned his baby as a way for mankind to enjoy unrestricted access to information, knowledge, and tools.
He remains distressed by how the internet is now a playground for powerful interests, from the government to corporations, each vying for control.
Speaking to Time magazine in 2014, Tim Berners-Lee stated: “Now, 25 years on [from the public release of the internet], web users are realizing they need human rights on the web … We need independence of the web for democracy, we need independence of the web to be able to support the press, we need independence of the web in general. It’s becoming very important to sort out all that.”
Unfortunately, we’re only sliding in the opposite direction.
How does internet censorship work?
Before diving into the topic of internet censorship, let’s backtrack slightly and understand how the internet functions in the first place.
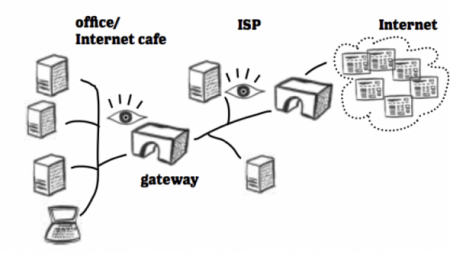
Source: Berkeley
Whenever you log on to the internet, you’re assigned an IP address by your internet service provider (ISP). That’s used to identify you as you traverse through the internet and keep tabs on your geographical location, the sites you visit, and other things you do online.
The problem with IP addresses is that while they’re an essential part of the internet, they can be used for nefarious purposes like spying and keeping tabs on your behavior. Even in the U.S., the loss of net neutrality means that ISPs can choose to slow down your connection (via throttling) to sites they don’t want you to visit. That’s an overt form of censorship, too.
In authoritarian countries like Saudi Arabia and Iran, censorship can take on a more chilling role. ISPs aren’t far removed from the government in such places, and it’s not like they can refuse state requests to hand over user data. Privacy and anonymity are alien concepts, so if netizens are caught indulging in activity that runs counter to state interests, there’s a high chance that they will face retribution for their acts.
Having said that, let’s come to the technicalities of how governments are able to censor content in the first place. As we outlined earlier, your ISP essentially controls the nodes between your computer and the internet.
Web infrastructure relies on equipment such as fiber optic cables, satellites, and underwater cables. This is what is referred to as the backbone of the internet, without which we’d simply go offline. Most ISPs connect to this backbone through gateways—and it is through this mechanism that they might be able to monitor or control user traffic.
Ways to conduct internet censorship
When we talk about internet censorship, it’s important to note that there isn’t a “one size fits all” strategy. Whether it’s your ISP, the government, or intelligence agencies, censorship can be conducted in a myriad of ways.
In some cases, your ISP may simply choose to “blacklist” certain sites via DNS servers. A DNS request matches domain names with website IP addresses, but this database can also be used as a censoring mechanism. For example, if your government wants to block Facebook, it can simply add the site to a blacklist preventing you from accessing its IP address.
Let’s take a closer look at other ways censorship is carried out.
IP blocking
IP blocking is similar to the blacklisting approach we highlighted earlier. In this situation, a system of surveillance servers monitors all website requests within a country or ISP. The servers scan each request against a list of sites that are deemed to be inaccessible. If you’re trying to reach one of these sites, the server will simply deny your request no matter how many times you click refresh.
If the blocked site is hosted on a shared server, then all the sites on that server will face the same fate.
Keyword filters
Keyword filters are a broader stroke taken by authoritarian governments and regimes to block internet chatter that they feel are detrimental to their interests.
For example, if the Iranian government wished to stop its citizens from reading about the protests that engulfed the country a couple of years ago, all it had to do was to identify keywords that users might be searching for. Any website URLs containing these keywords would be scrubbed and banned.
Keyword filtering is applied when authorities can’t identify specific sites but are aware that there’s a plethora of information that they need to block. Websites can come online in a matter of hours, making it difficult for agencies to continually monitor new ones.
Deep packet inspection
Deep packet inspection is an incredibly sophisticated strategy to impose censorship and relies on inspecting the content of each site as it loads on your browser.
Whenever you type in a website request on your browser, the ensuing data transfer takes place in smaller chunks known as packets. Deep packet inspection analyzes the contents of each packet, usually against a list of keywords to determine whether the site should open for the end user.
If the software determines that the site is inadmissible, it’ll cause the connection to drop instantly. The end user might receive an error message or simply a blank screen in this situation.
Speed malfunctions
The strategies mentioned above are the most commonly used techniques to impose internet censorship, but there are other ways to frustrate internet users, too. Some corporations might throttle your internet connection and make it incredibly slow and cumbersome to reach certain sites.
This approach has been used by ISPs in the past to restrict access to peer-to-peer sites such as uTorrent and Limewire.
Internet censorship in daily life
Some companies may also choose to restrict access to certain sites at the workplace. For example, the use of Facebook, Twitter, and YouTube might be frowned upon—in this case, it’s possible to blacklist individual port numbers.
In other situations, the hardware itself might contain certain programs that act as filtration and detection mechanisms. This is used in places like public libraries, universities, and schools where they don’t want people accessing pornographic sites or hate material. Some may also ban the use of the Tor browser so that users can’t try to access the Deep Web.


























Comments
You fail to mention active mitma psyop/gangstalkimg attack by a lowly aphabet tribe sponsored asu aka (mini silicon valley) attacks on T.I.’s…There’s a practice of this behavior at the asu property called “SkySong” ;’-p
Can you expand on the use of VPNs when it comes to Internet Security and the security measures you’ve mentioned.
I also us duckduckgo to search the web, can it be affected by the security measures you mentioned.
Hi Dennis, VPNs keep you safe and protected on the internet. Here’s an explainer.
As for DuckDuckGo, it’s only a web browser that promises not to track your personal data. Other than that, ISPs can certainly throttle and restrict access to it as well as apply additional security measures. Hope that helped!
Well when your not on the Targeted Individual end of the proverbial “space based weapons”. Than I would concur the best/ideal setup that would run from a rom, or plausible non-volatile storage device would be an md5 and/or SHA passed image of a linux distro tailored for your personal “interweb’s needs”. Soo would at least revert or load to the same initial configuration as was the time booted/used before….I’ve seen what quantum entanglement perhaps plausible deniability akin to plausible quantum a.i. or rtificial intelligence neural networks per se rather “mind/body” 😉 in real-time. Generate! You’ve been enlightened! Godbless, and live long & prosper! – jth
Enjoyed reading your article. Thanks!
Thailand
Very helpful.Thank you
Ok
I found the above info to be most helpfull.
Thanks
Thanks for reading, Peter!
Thanks
Tim Berners-Lee created the World Wide Web.
Indeed he did!
fsdfsd